21 Examples of Tech that Show How Society May Be Doomed
Carly Tennes
Published
08/21/2024
in
creepy
Though we may use it for Wordle, YouTube videos and occasionally sending a work email or two, the internet isn't just fun and games. Despite elaborate privacy policies and promises to keep our data locked away, the net as we know it is teeming with suspicious activity, ones that make the events of Mr. Robot look like a first-grade typing course.
From the true cost of "free" charging stations to the dangers of solar flares, here are 21 creepy tech facts that prove we are most definitely headed in the wrong direction.
- List View
- Player View
- Grid View
Advertisement
-
1.
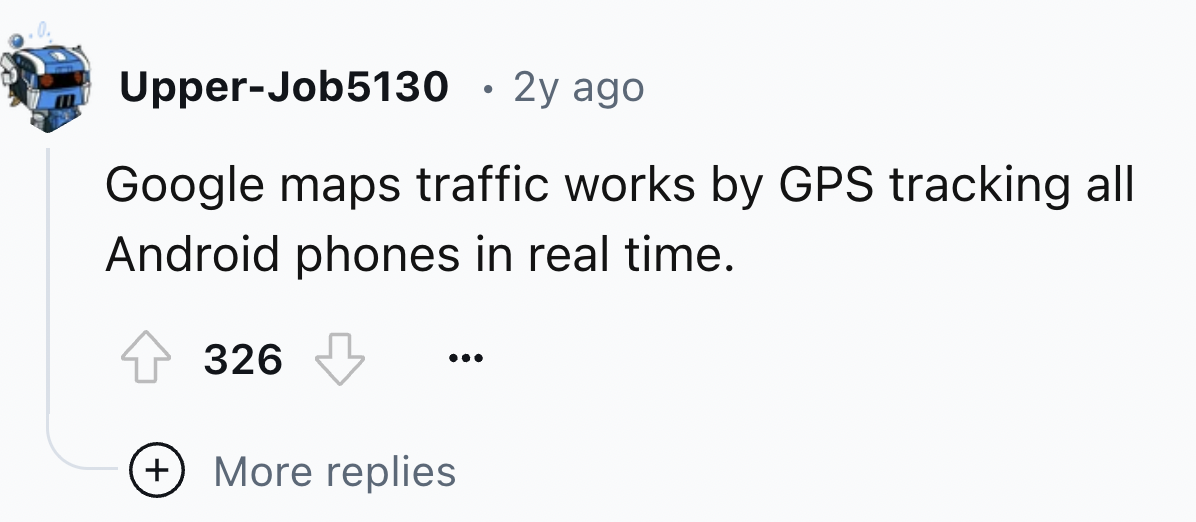
-
2.
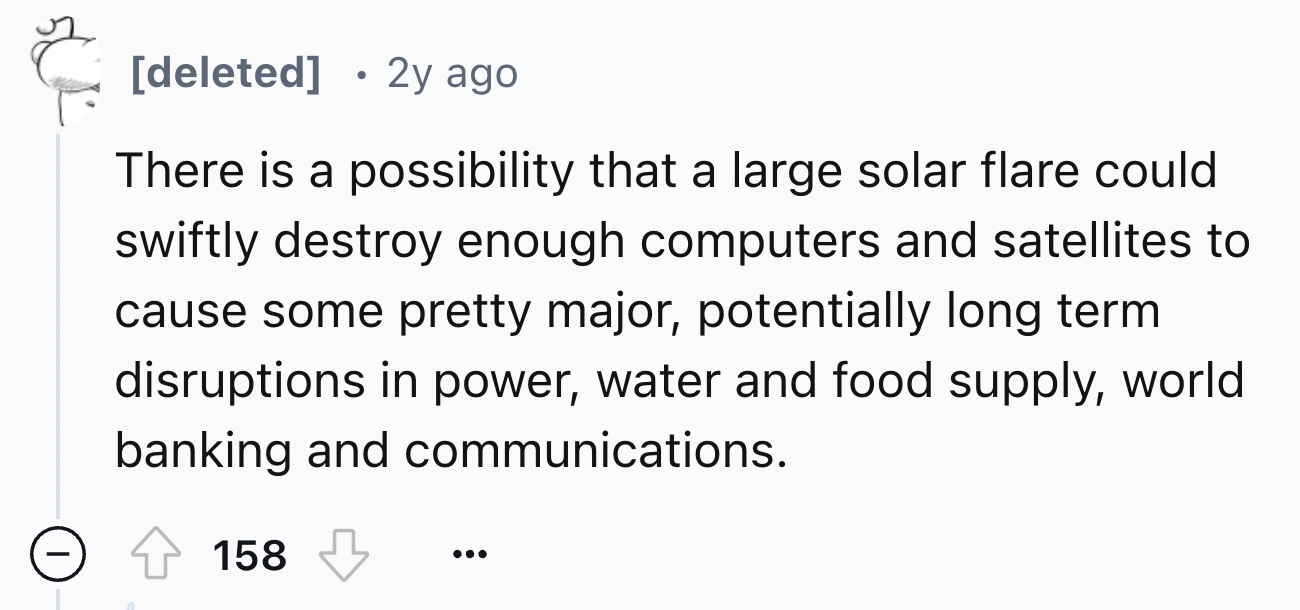
-
3.
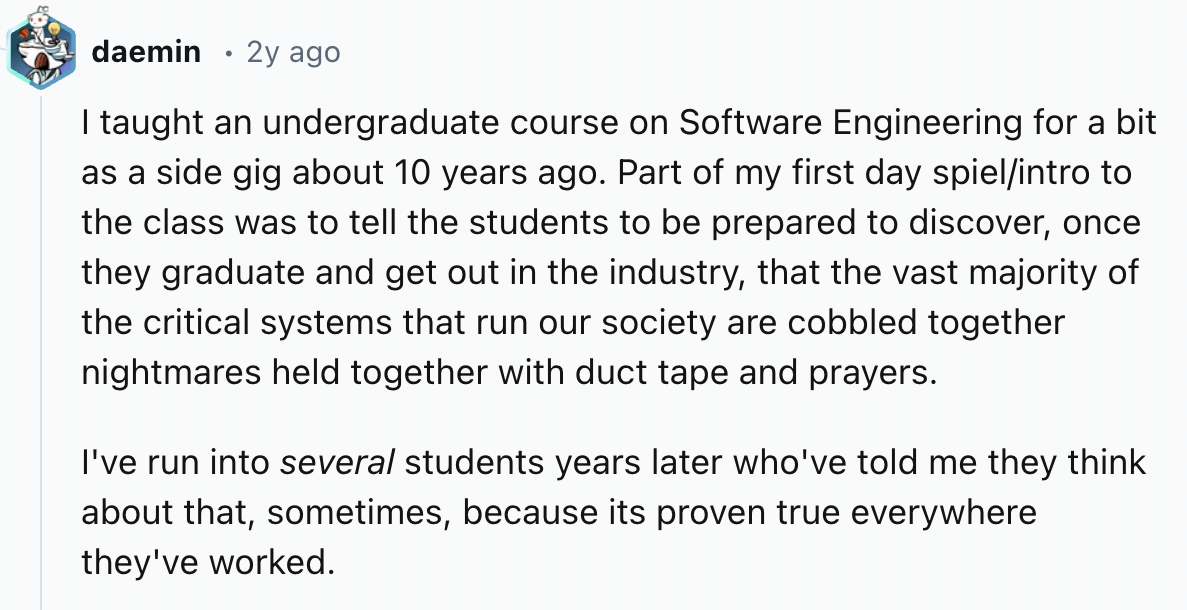
-
4.
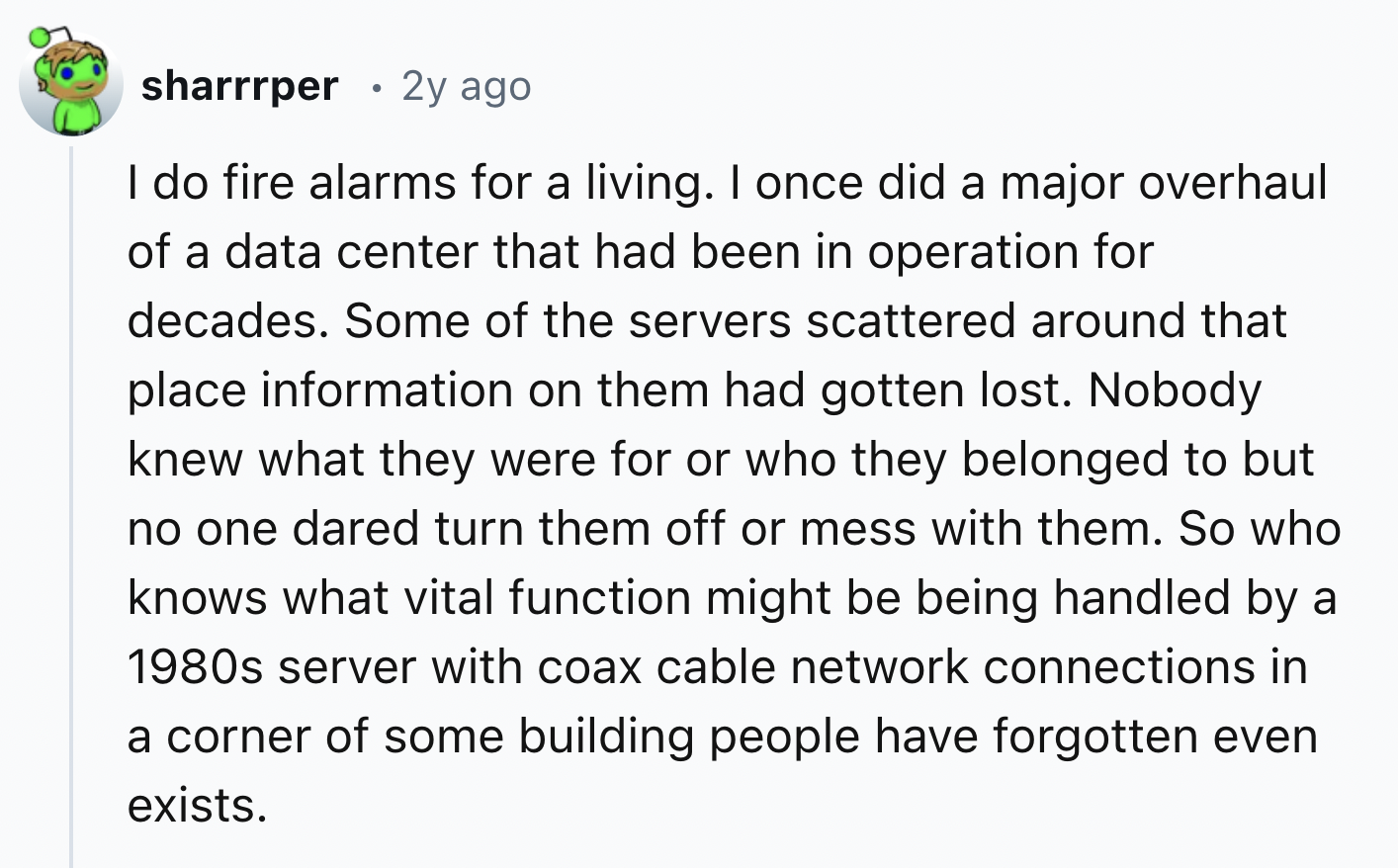
-
5.
-
6.
 “Juice J—king is a type of cyberattack where public USB charging points double as data connection points, installing malware or copying data. Free USB charging points can be used to steal your data.”
“Juice J—king is a type of cyberattack where public USB charging points double as data connection points, installing malware or copying data. Free USB charging points can be used to steal your data.” -
7.
-
8.
 “The average value of a person's data is about 30 cents.”
“The average value of a person's data is about 30 cents.” -
9.
-
10.
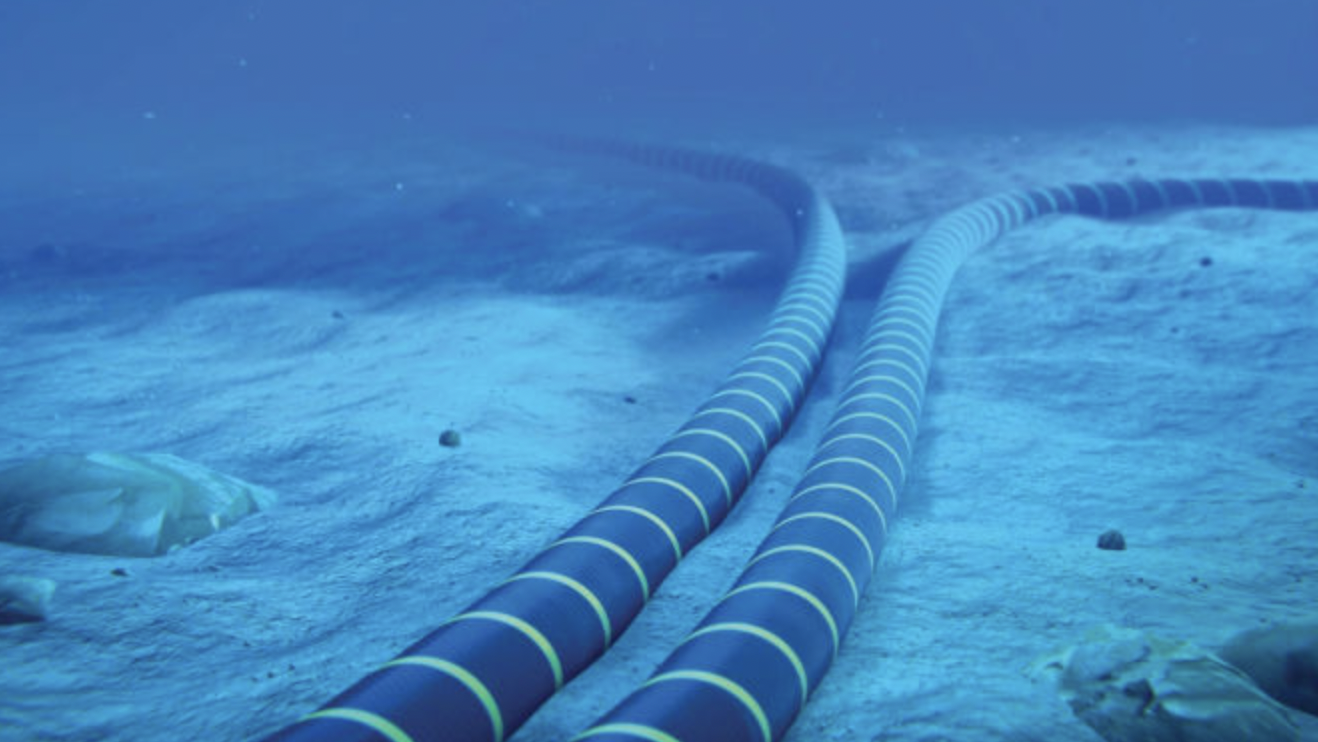 “Most internet data is not transferred across continents by satellites. Instead, 97% of intercontinental data is transferred through hundreds of thousands of miles of cables at the bottom of the ocean.”
“Most internet data is not transferred across continents by satellites. Instead, 97% of intercontinental data is transferred through hundreds of thousands of miles of cables at the bottom of the ocean.” -
11.
 “Seven people possess physical keys to the internet. By combining at least 5 of them, they may together control the authenticity of the internet.”
“Seven people possess physical keys to the internet. By combining at least 5 of them, they may together control the authenticity of the internet.” -
12.
 “47% of all internet traffic came from bots in 2022.”
“47% of all internet traffic came from bots in 2022.” -
13.
 “Reading all privacy policies the average internet consumer encounters in a year would take 76 work days.”
“Reading all privacy policies the average internet consumer encounters in a year would take 76 work days.” -
14.
-
15.
 “The Internet weighs the same as a strawberry: The weight of all the electrons in motion that make up the internet at any one moment is equivalent to 50 grams.”
“The Internet weighs the same as a strawberry: The weight of all the electrons in motion that make up the internet at any one moment is equivalent to 50 grams.” -
16.
-
17.
 “Rich kids bragging on social media, such as Instagram, are unwittingly providing incriminating evidence for prosecutors about their parents' fraud schemes. Cybersecurity firms say they have been using social media evidence to nail fraud and assets in up to 75 percent of their cases.”
“Rich kids bragging on social media, such as Instagram, are unwittingly providing incriminating evidence for prosecutors about their parents' fraud schemes. Cybersecurity firms say they have been using social media evidence to nail fraud and assets in up to 75 percent of their cases.” -
18.
 “Canadians have no privacy on the internet because of Bill C-30. This bill is to protect children from internet predators, but ‘children’ and ‘internet predators’ are ONLY mentioned in the title.”
“Canadians have no privacy on the internet because of Bill C-30. This bill is to protect children from internet predators, but ‘children’ and ‘internet predators’ are ONLY mentioned in the title.” -
19.
 “A company providing IP geolocation data assigned 300 million IP addresses to a rural Kansas farmhouse. This led to countless visits by police trying to find missing people, hackers, identity fraudsters and stolen cars.”
“A company providing IP geolocation data assigned 300 million IP addresses to a rural Kansas farmhouse. This led to countless visits by police trying to find missing people, hackers, identity fraudsters and stolen cars.” -
20.
 ‘A hacker was able to recreate the fingerprint of the German Defense Minister from a photograph. This is the same hacker who defeated Apple's thumbprint verification within 24 hours of the release of the iPhone 5S.”
‘A hacker was able to recreate the fingerprint of the German Defense Minister from a photograph. This is the same hacker who defeated Apple's thumbprint verification within 24 hours of the release of the iPhone 5S.” -
21.
 “The Kremlin had such a hard time with computer security that in 2013 they bought typewriters to prevent leaks.”
“The Kremlin had such a hard time with computer security that in 2013 they bought typewriters to prevent leaks.”
Categories:
Creepy










22 Comments